Be prepared for cyber threats with Valmet cybersecurity services
Dec 18, 2020
Connected production environments and critical infrastructures are increasingly experiencing cyberattacks. That is why it is of utmost importance to maintain the security level of automation systems and keep them up to date. Valmet offers its automation customers cybersecurity services that help them to secure their business continuity and, in the worst case, to quickly recover from a cyberattack.

Valmet’s long history in the digitalization of process industries and power plants traces back to the 1960s, and it has been developing its digital solutions offering continuously since then. This is an advantage in today’s connected and integrated production environments where we face totally new types of business continuity threats in the form of cyberattacks.
Process automation systems are critical for the reliable operation of production plants and thus ever-more tempting targets for cyberattacks. This means that companies must secure not only the Information Technology (IT) they use, but also take care of the security of their Operational Technology (OT) – i.e. the process automation systems. There are already several examples of “successful” attacks that have closed entire production plants or have led to payments of large ransoms to avoid production stops.
Creating secure production environments
Valmet DNA Cybersecurity Services are designed to support customers in creating and maintaining a secure production environment. In addition, Valmet’s cybersecurity consulting cover a recovery planning service for fast recovery after a possible attack and a crisis exercise service.
“Our starting point is that our automation systems are secure at the point of delivery. Through a service agreement, customers can be confident that that is the case also after the system is handed over to them,” says Teemu Kiviniemi, Solution Manager at Valmet.
Valmet constantly follows the latest information on security threats and malware released by leading information security actors – like Microsoft, CERT-FI and ICS-CERT – and acts as needed based on that information.
”Valmet Automation has received an information security certificate for meeting the criteria of Information Security Management System standard ISO/IEC 27001:2013. In addition, our product development methods have been certified with the IEC 62443-4-1 and ISASecure Security Development Lifecycle Assurance (SDLA) cybersecurity certificates. These certifications mean that our own processes are proven to be secure.”
“We know our Valmet DNA automation system more thoroughly than anyone else, and we are able to quickly evaluate which cyber threats can have an effect on it. And after testing, we can deliver the needed updates automatically to our customers,” Kiviniemi explains.
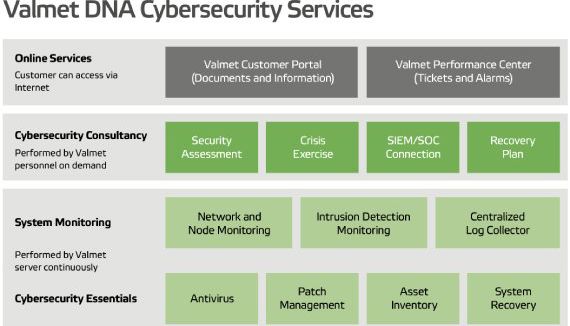
Services to secure automation system availability and business continuity
Valmet offers two agreement-based cybersecurity services to its automation customers: Valmet DNA Cybersecurity Essentials and Valmet DNA System Monitoring.
Valmet DNA Cybersecurity Essentials is a service that keeps the customer’s system security level up to date almost automatically. It includes antivirus software, patch management, asset inventory, and system recovery related services. It is independent of the Valmet DNA version used because it is based on a virtual machine image, Valmet Cybersecurity Server.
Valmet DNA System Monitoring includes network and node monitoring as well as intrusion detection monitoring and centralized log monitoring. The system recognizes anomalies in the DNA system network traffic and alarms when it detects something unusual. However, the human brain is still needed to interpret the finding.
“Intrusion detection monitoring has become quite topical; in some business areas and markets, it is already a must and also a requirement from the authorities’ side. We see it becoming a standard-like feature in cyber-secured systems in the near future,” Kiviniemi says.
It pays to be prepared
Despite all the cybersecurity preparations, systems and trainings, sometimes the hostile cyberattacks are successful. In these worst-case situations, it is fundamentally important to have a proper automation system recovery plan.
A company’s business continuity plan should always include an automation system recovery plan.
“Our cybersecurity consulting services produce tailor-made recovery plans for our customers; and it is something we do a lot of nowadays. As we see it, a company’s business continuity plan should always include an automation system recovery plan,” Kiviniemi tells. Another popular consulting service Valmet offers is a cyberattack crisis exercise. “These exercises are often real eye-openers for plant management. The threat is there; it is real. So it pays to be prepared.”
Valmet Cybersecurity Foundation training
Valmet DNA Cybersecurity Foundation is a one-day training that offers customers a detailed review of a Valmet DNA automation system’s cybersecurity architecture and controls and services.
After the training, the participants will be aware of different cyberthreats and will know how ICS/OT environments can be protected against typical malicious attacks by using Valmet DNA Cybersecurity solutions and services.
The areas addressed during the training are:
- Cybersecurity fundamentals in Industrial Control Systems, IT versus OT
- Typical attack vectors and tactics used today
- Technologies needing protection
- Asset Inventory and Lifecycle planning
- Endpoint Protection (Hardening, Antivirus, Patch Management, Whitelisting, etc.)
- Network monitoring (Network Segmentation, Firewalls,
IDS/IPS, etc.) - Remote connections (Valmet SCS and Secomea)
- Recovery planning in preparing for disaster recovery
- Cybersecurity exercise
Text Sanna Haanpää-Liukko
Information Technology (IT)
Information Technology (IT) means the technologies used to process information, including software, hardware, communication technologies, and related services. IT does not control any processes. Security updates are done often. The leading information security companies release their patches approximately once a month (“Patch Tuesday”) – and company IT departments then decide when to launch them within their own organizations. Systems in an IT environment get replaced with new versions every few years.
Operational Technology (OT)
OT refers to hardware and software that monitors or controls physical devices, machines, processes, and events in the company, like an automation system does. OT-related security updates are done far less frequently than in IT side, because operations or production cannot be stopped only because of updates. An OT -system lifecycle is normally counted in decades.
Today, OT and IT are merging at ever-increasing speed, driven by virtualization, mobility and the cloud.

